Fort
|
As groundbreaking leaders in personal security and risk management for travelers, we stand ready to equip and serve as you are called to the ends of the Earth.
|
ARE YOU PREPARED?
|
|
|
TIPS & ADVICE

Top 10 List Of The Day!
We’re in a world that the internet is a double-edged sword, offering endless opportunities for learning and entertainment, but also posing significant risks to children's safety and well-being (many adults too).
Here are ten practical tips to help protect your children in the virtual world:
1. Open Communication: Maintain an open dialogue about their online activities and encourage them to share any concerns.
2. Educate on Privacy: Teach kids the importance of not sharing personal information like addresses, phone numbers, or school details.
3. Use Strong Passwords: Ensure they create strong, unique passwords for their accounts and understand the need to keep them confidential.
4. Set Boundaries: Establish clear rules about the types of websites they can visit and the amount of time they can spend online.
5. Monitor Activity: Regularly check their browsing history and the apps they use. Utilize parental control tools to help manage their online experience.
6. Safe Social Media Practices: Guide them on setting privacy settings on social media and understanding the risks of talking to strangers.
7. Recognize Cyberbullying: Educate them on what cyberbullying and inappropriate content is and encourage them to report any incidents.
8. Avoid Phishing Scams: Teach them to recognize suspicious emails and messages and never to click on unknown links.
9. Encourage Critical Thinking: Help them understand that not everything they see online is true and to question the source of their information.
10. Lead by Example: Model good online behavior and share your own experiences and best practices.
By implementing these tips, you can help ensure a safer online environment for your children.
The goal is not to instill fear or anxiety, but to empower your kids to navigate the digital world with confidence and caution.
We’re in a world that the internet is a double-edged sword, offering endless opportunities for learning and entertainment, but also posing significant risks to children's safety and well-being (many adults too).
Here are ten practical tips to help protect your children in the virtual world:
1. Open Communication: Maintain an open dialogue about their online activities and encourage them to share any concerns.
2. Educate on Privacy: Teach kids the importance of not sharing personal information like addresses, phone numbers, or school details.
3. Use Strong Passwords: Ensure they create strong, unique passwords for their accounts and understand the need to keep them confidential.
4. Set Boundaries: Establish clear rules about the types of websites they can visit and the amount of time they can spend online.
5. Monitor Activity: Regularly check their browsing history and the apps they use. Utilize parental control tools to help manage their online experience.
6. Safe Social Media Practices: Guide them on setting privacy settings on social media and understanding the risks of talking to strangers.
7. Recognize Cyberbullying: Educate them on what cyberbullying and inappropriate content is and encourage them to report any incidents.
8. Avoid Phishing Scams: Teach them to recognize suspicious emails and messages and never to click on unknown links.
9. Encourage Critical Thinking: Help them understand that not everything they see online is true and to question the source of their information.
10. Lead by Example: Model good online behavior and share your own experiences and best practices.
By implementing these tips, you can help ensure a safer online environment for your children.
The goal is not to instill fear or anxiety, but to empower your kids to navigate the digital world with confidence and caution.
 THIS IS A SAMPLE NOT BE USED!
Yes we had to say it for somebody
THIS IS A SAMPLE NOT BE USED!
Yes we had to say it for somebody
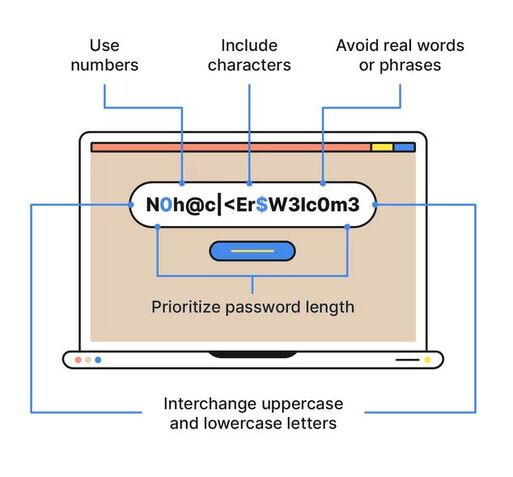
Password Hacking CONTINUES To Rise. How Secure Is Yours?
With so much of our lives online – from banking and emails to health records and passport details – it’s important to keep your digital life secure. A great action that everybody should be doing (but may be lacking) is using strong passwords.
Here’s 5 tips to making your passwords more secure:
1. Don’t include anything in your password that is personal to you or describes you. Not your name, birthdate, address, phone number, etc)
2. Longer passwords are better so make sure they are OVER 15 characters.
3. Use different passwords for different accounts. If one gets hacked or leaked, you don’t want them all to fall when it gets posted online.
4. Use a phrase or random string of characters. Don’t use proper nouns or real words found in dictionaries. Be random with characters - Upper, Lower, Numbers, Symbols
5. Activate two-factor authentication on your accounts. Passwords alone can be guessed and phished and, once stolen, tried against a range of accounts to find more access.
With so much of our lives online – from banking and emails to health records and passport details – it’s important to keep your digital life secure. A great action that everybody should be doing (but may be lacking) is using strong passwords.
Here’s 5 tips to making your passwords more secure:
1. Don’t include anything in your password that is personal to you or describes you. Not your name, birthdate, address, phone number, etc)
2. Longer passwords are better so make sure they are OVER 15 characters.
3. Use different passwords for different accounts. If one gets hacked or leaked, you don’t want them all to fall when it gets posted online.
4. Use a phrase or random string of characters. Don’t use proper nouns or real words found in dictionaries. Be random with characters - Upper, Lower, Numbers, Symbols
5. Activate two-factor authentication on your accounts. Passwords alone can be guessed and phished and, once stolen, tried against a range of accounts to find more access.





